- Topic1/3
14k Popularity
34k Popularity
17k Popularity
6k Popularity
174k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is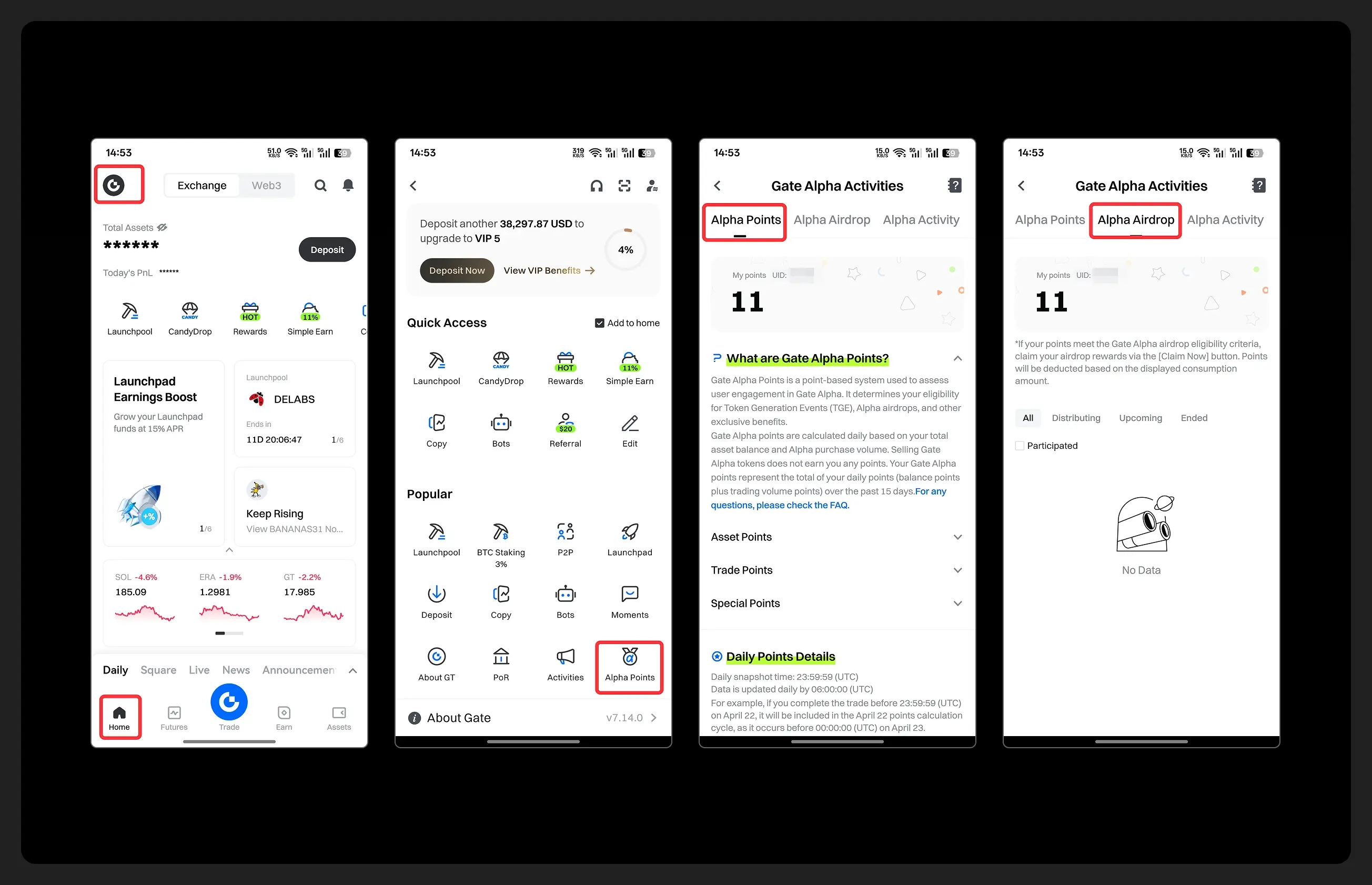
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Solo breaks through the Web3 identification dilemma: zkHE technology leads a new paradigm of trusted anonymity.
New Paradigm of Web3 Identification Layer: Solo's Technical Breakthrough and Ecological Layout
The Web3 identification layer project Solo recently completed a $1.2 million Pre-Seed round of financing, led by Draper Associates. Solo is building a "trustworthy anonymous" on-chain identification system based on its original zkHE architecture, which is expected to break the long-standing "impossible triangle" that has plagued Web3, achieving a balance between privacy protection, identification uniqueness, and decentralized verifiability.
The core team of Solo is quite strong. CEO Edison studied at Yale School of Management and co-founded the Yale Blockchain Association. The other two co-founders, Stephen and Sissi, are both professors at Shenzhen University, with substantial experience in the fields of blockchain and artificial intelligence respectively.
In terms of technical path, Solo is centered around its unique zkHE( zero-knowledge homomorphic encryption) scheme, constructing a set of identity architecture that achieves a dynamic balance between privacy protection, identification uniqueness, and decentralized verifiability. In the current context where the Web3 ecosystem is generally facing systemic issues such as frequent witch attacks, lack of user reputation systems, and difficulties in compliance access, the scheme proposed by Solo may hold significant reference and leadership significance.
The Long-term Absence of Web3 Identification Layer
Although the infrastructure in the Web3 space is rapidly improving, the "identification layer" has long been in a state of absence as a key module supporting trust and participation. From the perspective of on-chain systems, users are usually just a wallet address composed of letters and numbers, lacking structured individual characteristics and behavioral tags. Without the support of additional identification layer mechanisms, the crypto-native world can hardly establish credible user profiles, let alone achieve reputation accumulation and credit assessment.
The absence of the identification layer has directly given rise to one of the most common and challenging issues in Web3, namely the witch attack. Taking Celestia as an example, in its 2023 airdrop, up to 65% of the 60 million $TIA tokens were acquired by bots or witch accounts, a similar phenomenon was also widely observed during the distribution processes of projects like Arbitrum and Optimism.
In the DePIN field, the phenomenon of submitting fake addresses and falsifying data to cheat incentives is common, disrupting the authenticity of data and directly affecting the practicality and trust foundation of the network. In GameFi, the behavior of using multiple accounts to complete tasks and claim rewards in bulk seriously undermines the balance of the in-game economic system, leading to the loss of real players and the failure of project incentive mechanisms.
In the field of AI, the absence of the identification layer has also had far-reaching effects. Currently, the training of large-scale AI models increasingly relies on "human feedback" and data annotation platforms, and these tasks are often outsourced to open communities or on-chain platforms. However, in the absence of guarantees for "human uniqueness," the phenomena of scripted batch simulation behaviors and robot-generated inputs have become increasingly severe, not only contaminating the training data but also greatly weakening the model's expressiveness and generalization ability.
Exploration of Web3 Identification Layer
Currently, there are dozens of Web3 identification layer solutions on the market, which can be roughly divided into four categories: biometric, social trust, DID aggregation, and behavior analysis.
Biometric types are typically characterized by biometric technology to ensure identity uniqueness, possess strong resistance to witch attacks, but are prone to infringing on user privacy. Social trust types emphasize "user sovereignty," highlighting social trust networks and open verification, but find it difficult to guarantee identity uniqueness. DID aggregation types construct on-chain identity structures by integrating Web2 identity/KYC data, Verifiable Credentials, and other external credentials, with high compatibility with existing compliance systems, but limited decentralization. Behavioral analysis types build user profiles and reputation systems based on on-chain address behavior, provide good privacy protection, but struggle to connect with users' real identities.
Existing identification layer solutions generally fall into the impossible triangle dilemma of privacy protection, identity uniqueness, and decentralized verifiability. Except for biometric solutions, the identity mechanisms in other sectors generally struggle to effectively ensure "identity uniqueness."
Solo's Technical Solution
Solo chooses biometric identification as the basis for the uniqueness of user identification, and based on cryptography, proposes a unique technological path around the balance dilemma between "privacy protection" and "decentralized verifiability."
The Solo solution is based on the zkHE architecture, integrating Pedersen commitments, homomorphic encryption (HE), and zero-knowledge proofs (ZKP). Users' biometric features can undergo multiple encryption processes locally, and the system generates verifiable zero-knowledge proofs and submits them to the chain without exposing any raw data, achieving the non-falsifiability of identification and verifiability under privacy protection.
In the homomorphic encryption stage, the system inputs the pledged biometric characteristics into the circuit in a homomorphic encrypted form, performing logical operations such as matching and comparison without the need for decryption throughout the process. After completing the encrypted calculations, Solo will locally generate a zero-knowledge proof (ZKP) for on-chain submission and verification. This ZKP proves that "I am a unique and real human being" without disclosing any original biometric information or intermediate calculation details.
Solo adopts the efficient Groth16 zk-SNARK as the proof generation and verification framework, generating concise and robust ZKP with minimal computational overhead. The verifier only needs to verify this proof to confirm the identification validity, and the entire process does not require access to any sensitive data. Ultimately, this ZKP is submitted to the exclusive Layer2 network SoloChain, where it is verified by on-chain contracts.
In terms of verification efficiency, the Solo solution itself possesses extremely high efficiency. When facing higher-dimensional biometric feature data, the zkHE architecture adopted by Solo significantly outperforms traditional ZKP solutions in proof generation time and total authentication duration. Under 128-dimensional data conditions, the authentication time for traditional ZKP exceeds 600 seconds, while the Solo solution remains largely unaffected, consistently maintaining within a few seconds.
New Attempts to Break the "Impossible Triangle" of Web3 Identification Layer
Solo provides a new path to break the "impossible triangle" of the Web3 identification layer, achieving a technological balance and breakthrough among privacy protection, identification uniqueness, and usability.
On the privacy level, the zkHE architecture allows all users' biometric features to be homomorphically encrypted and ZKP constructed locally, without the need to upload or decrypt the original data throughout the process, thus completely avoiding the risk of privacy leakage. In terms of identity uniqueness, Solo confirms whether the current verifier is the same person as in historical registration records through a feature vector distance comparison mechanism under encrypted state, establishing the fundamental identity constraint of "each address is backed by a real unique human." On the usability level, Solo ensures that all computational tasks can be completed on ordinary mobile devices through fine optimization of the zk proof process, with verification generation time usually controlled within 2-4 seconds, while on-chain verification can be completed in milliseconds and is fully decentralized.
Solo has reserved compliance docking interfaces in its system design, including optional bridging modules that support integration with on-chain DID and KYC systems, as well as the ability to anchor verification status to a designated Layer 1 network in specific scenarios. In the future, when entering the compliance market, Solo is expected to meet the requirements for identification, data traceability, and regulatory cooperation in various regions while maintaining privacy and decentralization features.
Compared to solutions that focus on upper-level identification tags or behavioral credentials, Solo's advantage lies in building a foundational identity network that can achieve "human uniqueness confirmation" at the lowest level, and has characteristics such as privacy protection, trustlessness, embeddability, and sustainable verification, providing basic "human authenticity verification" for higher-level VC, SBT, social graphs, etc.
Currently, Solo has partnered with multiple protocols and platforms, including Kiva.ai, Sapien, PublicAI, Synesis One, Hive3, GEODNET, etc., covering various vertical tracks such as data labeling, DePIN networks, and SocialFi games. These collaborations are expected to further validate the feasibility of Solo's identification mechanism, providing a feedback mechanism for calibrating real-world demands for its zkHE model, helping Solo continuously optimize user experience and system performance.
By building a trustworthy and anonymous identification layer system for the Web3 world, Solo is laying the capability foundation for 1P1A and is expected to become an important underlying infrastructure to promote the evolution of on-chain identification systems and the expansion of compliant applications.